Hubgrade Connectivity
This document describes our secure standard practice when implementing the Hubgrade Wastewater Plant Performance and the Hubgrade Sewer Performance modules (hereinafter called Hubgrade) covering how to integrate the OPC Bridge, what network to place it on, using DMZ, the function of the watchdogs and what kind of work, that needs to be done in the PLC area.
Hubgrade is designed to enforce the following security principles
Hubgrade follow best practices regarding IS security.
All connections between Hubgrade and Customer network are outbound from the customer network, through Customer firewall. No incoming connections are established.
Hubgrade does not have a direct connection to PLCs.
PLC’s are autonomous and will continue operation independently of connection loss to Hubgrade.
Customer data is authenticated and encrypted by dedicated customer specific certificates.
Each customer data set is segregated from each other.
Each user has a distinguished role and user rights.
Hubgrade IT uses Veolia best practice in security operations.
Hubgrade is guarded by AWS security best practices.
The frontend is encompassed by the functionalities used directly by users.
The connectivity is done by an OPC UA server which the plant’s OPC infrastructure sends measurements to and requests regulation set points from.
The backend handles the calculation of the regulation set points and is completely shielded by the frontend.
Hubgrade Security Practice
Hubgrade cybersecurity is based on Veolia cybersecurity policy and organisation. Our cybersecurity is based on guidelines set forth by leading security standards like ISO/IEC 27002:2013, NIST SP 800-210 and NIST Cybersecurity Framework 1.1 in addition to numerous other publications, guidelines and industry 4.0 best practices.
As additional security control, specific for the provided solution, Hubgrade undergoes internal and external periodic security tests, including scans for known vulnerabilities, assessment against best practise on secured architecture , including implementation review and penetration tests.
The processes of the application development, operation and support organisation is certified under ISO 9001.
The IT infrastructure that Amazon Web Services (AWS) provides to its customers is designed and managed in alignment with best security practices and a variety of IT security standards. The following is a partial list of assurance programs with which AWS complies: SOC 1/ISAE 3402, SOC 2, SOC 3, FISMA, DIACAP, and FedRAMP, PCI DSS Level 1, ISO 9001, ISO 27001, ISO 27017, ISO 27018.
NIS2 Regulation Compliance
Hubgrade enable your organisation to comply with NIS 2 regulation according to Article 21, Cybersecurity risk-management measures;
Hubgrade connectivity and service is done with network security and information systems and in the physical environment protecting your environment of security incidents, the service include the following as required by the article:
Policies on risk analysis and information system security that are defined by Veolia in accordance with NIST (as well as leading security standards like ISO/IEC 27002:2013, etc)
Incident handling.
Business continuity, such as backup management and disaster recovery, and crisis management.
Supply chain security with all critical components and operational environment of the service.
Security in network and information systems acquisition, development and maintenance, including vulnerability handling and disclosure.
Policies and procedures to assess the effectiveness of cybersecurity risk-management measures under the governance of Veolia.
Basic cyber hygiene practices and cybersecurity training of the involved Veolia employees.
Policies and procedures regarding the use of cryptography and, where appropriate, encryption.
Human resources security, access control policies and asset management provided by Amazon Web Services (AWS) .
Available integration of your company multi-factor authentication, where appropriate.
Hubgrade standard terms and conditions commit to the compliance with all relevant customer sectoral regulations.
Hubgrade Building Blocks
Hubgrade consist of a Front-end, Connectivity interface and a Backend. The Frontend is encompassed by the functionalities used directly by the users. The connectivity is done by an OPC UA server which the plant’s OPC infrastructure sends measurements to and requests regulation set points from. The Backend handles the calculation of the regulation set points and is completely shielded by the Front-end.
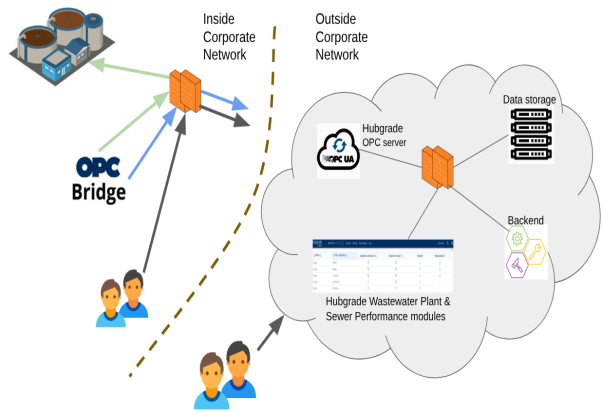
User access is centrally validated and each of the Front-end functionalities authorise the users based on the role that the users have been given.
All user management - including access rights - are managed by the customer administrator account. The customer creates and revokes user accounts for his/her own staff
Backend Data for each plant are separated in different database schemas and data processing is separated within dedicated containers.
It is the customer’s OPC infrastructure that initiates the connection with Hubgrade and the customer has therefore full control with the connection - when it is established and to what IP-address.
Hubgrade cannot establish an inbound connection to the plant.
The OPC UA communication is secured and encrypted through certificates and can therefore not be tampered by 3rd party.
Establishing the OPC UA connection requires user-id/password and certificate that matches the specific plant.
User communication is secured through the use of encryption (the HTTPS protocol)
The communication between Front-end functionalities and from the Frontend to the Backend is also secured using HTTPS and functionality specific access control (access to one functionality does not necessarily give access to other functionalities)
Elevated Security Option
Hubgrade is - as described in the previous sections - designed and implemented with security as the main driver. This includes security related to accessibility, scalability, robustness, resilience and cybersecurity.
OPC Bridge ensures that there is no cloud connectivity to the PLC network.
The cybersecurity aspects of the solution is further enhanced by securing the OPC-bridge in a separate DMZ, thereby isolating the PLC and SCADA, by the introduction of an OPC bridge installed at a separate network at the plant DMZ.
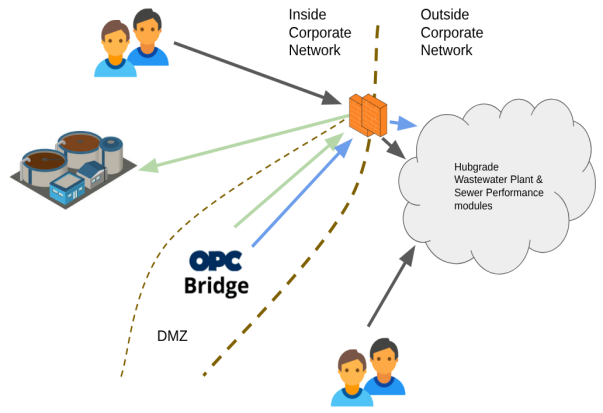
The OPC-Bridge now also acts as a proxy for the plant’s communication with the Hubgrade OPC UA server - transmitting measurements and requests for set points from the plant through the gateway.
From a cyber security perspective this solution strengthens the protection of the plant’s PLC network by shielding it behind a DMZ as the direct communication between the PLC network and the cloud service is terminated. The DMZ should be configured so that it only allows outbound communication to the cloud end-point and only allows out-bound communication to the OPC server at the plant.
Communication validation by using keep-alive signal
During Hubgrade implementation the PLC engineers and the Hubgrade team validate each optimisation feature and the PLC tags, that are retrieved and set for the optimisation process.
The Hubgrade UA OPC server publishes a keep alive signal to ensure that Hubgrade is online. In case the PLC has not received an updated value in the keep-alive signal within a specified period of time, the PLC shall assume that the connection between Hubgrade and the PLC has been lost. In such case the PLC shall disregard Hubgrade setpoints and revert to PLC-based controlling.
To validate the connection from PLC to Hubgrade, the PLC must send a keep-alive value tag, in order for Hubgrade to verify the communication. Hubgrade will notify users when communication is lost.
Configuration of the PLC system with Watchdogs
Hubgrade requires modifications in the customer’s PLC/SCADA in order to use set points from the optimisation features. The modifications objective is to; Implement watchdog strategy in PLC to operate either by setpoint from Hubgrade or as stand-alone.
The PLCs regulate the customer’s equipment (pumps, blowers, dosing equipment, etc) when setpoints are retrieved from Hubgrade or from local default settings.
Customer data
To minimise access to customer and user data, customer is always responsible for the following;
Security control of the connectivity inside the customer network. Account administration, user accounts lifecycle; Assigning administrator who controls all users and access to customer plants and equipment. Control of feature settings by such as review logs of changes made by users. Control of change requests.
Operation and Support
To ensure optimal operational, the Hubgrade service includes the monitoring and alerts of customers with regards to communication issues. The service monitors for communication breakdown between the Hubgrade service in AWS cloud and the OPC bridge that is deployed at the customers site.
The customer is to identify a contact person that has the relevant technical competences; To ensure that the OPC bridget software is up-to-date, and connected to the OPC in the AWS cloud, and that there are no connectivity issues with the customer network and equipment. The serviceteam will alert the customer contact, to investigate and resolve incidents.
Final words
Hubgrade implements industry-leading practices to optimize PLC automation and ensure seamless operational continuity across plant operations and sewer systems.
By Secured cloud practices, using certificates and standard protocols such as OPC UA to secure communications, by using segregated network security for isolating the cloud from the plant and the users from data, and by using logical controls, watch dogs functionality.
We can ensure that the plant environment is operational and secure, and plant operators are always in control.
